20.1: Information Technology Trends
20.1.1: Hardware and Software Improvements
To keep up with evolving consumer and market trends, both hardware and software components have seen drastic improvements.
Learning Objective
Outline the recent technology trends in both hardware and software improvements
Key Points
- Unlike standard RAM computer memory, in which the user supplies a memory address and the RAM returns the data word stored at that address, a CAM is designed such that the user supplies a data word and the CAM searches its entire memory to see if that data word is stored anywhere in it.
- CMOS logic gates have allowed computing to become a commodity which is now ubiquitous—embedded in many forms, from greeting cards and telephones to satellites.
- Improvements in software can largely be attributed to the implementation of software development models, such as the waterfall model, the spiral model, and agile software development.
Key Terms
- CMOS
-
Complementary metal–oxide–semiconductor (CMOS) is technology for constructing integrated circuits. CMOS technology is used in microprocessors, microncontrollers, static RAM and other digital logic circuits.
- CPU
-
The main computer case containing the central components of a personal computer.
Today’s technology is rapidly evolving. To keep up with consumer and market trends, both hardware and software components have seen drastic improvements.
Hardware Improvements
The 21st century has seen the rise of multi-core CPUs. Content-addressable memory (CAM) has become inexpensive enough to be used in networking. CAM is a special type of computer memory used in certain very high speed searching applications. Unlike standard computer memory (random access memory or RAM) in which the user supplies a memory address and the RAM returns the data word stored at that address, a CAM is designed such that the user supplies a data word and the CAM searches its entire memory to see if that data word is stored anywhere in it. If the data word is found, the CAM returns a list of one or more storage addresses where the word was found. Because a CAM is designed to search its entire memory in a single operation, it is much faster than RAM in virtually all search applications.
CMOS logic gates have allowed computing to become a commodity which is now ubiquitous—embedded in many forms, from greeting cards and telephones to satellites. Fiber-optic and photonic devices, which already have been used to transport data over long distances, are now entering the data center—side by side with CPU and semiconductor memory components. This allows the separation of RAM from CPU by optical interconnects.
Software Improvements
Improvements in software can largely be attributed to the implementation of software development models. One example is the waterfall model . The waterfall model shows a process where software developers are to follow these phases in order:
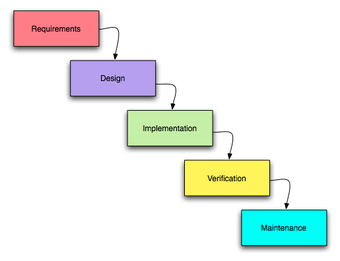
The Waterfall Model
A diagram laying out the steps of the waterfall model for software development.
- Requirements specification (Requirements analysis)
- Software design
- Implementation and Integration
- Testing (or Validation)
- Deployment (or Installation)
- Maintenance
Reviews may occur before moving to the next phase, which allows for the possibility of changes. Reviews may also be employed to ensure that the phase is indeed complete. The phase completion criteria are often referred to as a “gate” that the project must pass through to move to the next phase. Waterfall discourages revisiting and revising any prior phase once it’s complete.
Another example is the spiral model . The key characteristic of a spiral model is risk management at regular stages in the development cycle. This model combines some key aspects of the waterfall model and rapid prototyping methodologies, but provides emphasis in deliberate iterative risk analysis, particularly suited to large-scale, complex systems. The spiral is visualized as a process passing through some number of iterations, with the four-quadrant diagram representative of the following activities:

Spiral Model
A diagram laying out the steps in the spiral model of software development.
- Formulate plans to identify software targets, implement the program, clarify the project development restrictions.
- Risk analysis or assessment of selected programs, to consider how to identify and eliminate risk.
- Implementation of software development and verification.
- Plan the next iteration.
The spiral model has some restrictive conditions, as follows:
- The spiral model emphasizes risk analysis, and thus requires customers to accept this analysis and act on it. This requires both trust in the developer as well as the willingness to spend more to fix the issues, which is the reason why this model is often used for large-scale internal software development.
- If the implementation of risk analysis will greatly affect the profits of the project, the spiral model should not be used.
- Software developers have to actively look for possible risks, and analyze it accurately for the spiral model to work.
The first stage is to formulate a plan to achieve the objectives with these constraints, and then strive to find and remove all potential risks through careful analysis and, if necessary, by constructing a prototype.
A third model is known as agile software development. Agile software development uses iterative development as a basis but advocates a lighter and more people-centric viewpoint than traditional approaches . Agile processes use feedback, rather than planning, as their primary control mechanism. The feedback is driven by regular tests and releases of the evolving software.

Agile Software Development
A poster outlining the principles of agile software development.
20.1.2: Consumerization of IT
Consumerization is the growing tendency for new IT to emerge first in the consumer market and then spread into business and government organizations.
Learning Objective
Explain the business and technology implications of consumerization in the technology industry
Key Points
- It was the growth of the World Wide Web in the mid 1990s that began the modern pattern of consumerization. In particular the rise of free, advertising-based services such as email and search engines.
- The primary impact of consumerization is that it is forcing businesses, especially large enterprises, to rethink the way they procure and manage IT equipment and services.
- Products have become easier to use, and cloud-based, software-as-a-service offerings are addressing an ever-widening range of business needs in areas such as video-conferencing, digital imaging, business collaboration, salesforce support and systems back-up.
- One of the more serious, negative implications of consumerization is that security controls have been slower to be adopted in the consumer space.
- The giant data centers that have been and are being built by firms such as Google, Apple, Amazon and others are far larger and generally much more efficient than the data centers used by most large enterprises.
Key Terms
- customer relationship management
-
Customer relationship management (CRM) is a widely implemented model for managing a company’s interactions with customers, clients and sales prospects.
- cloud
-
Regarded as an amorphous omnipresent space for processing and storage on the Internet; the focus of cloud computing.
- server
-
A computer or a program which provides services to other programs or users, either in the same computer or over a computer network.
Consumerization is the growing tendency for new information technology to emerge first in the consumer market and then spread into business and government organizations. The emergence of consumer markets as the primary driver of information technology innovation is seen as a major IT industry shift, as large business and government organizations dominated the early decades of computer usage and development .
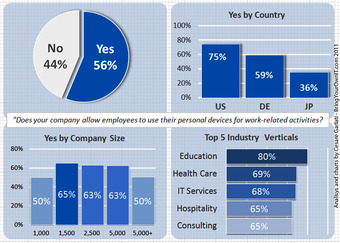
Consumerization Facts – Part 1
A survey was conducted in June 2011 in the U.S., Germany and Japan among IT personnel. It found that consumerization has reached a tipping point.
It was the growth of the World Wide Web in the mid 1990s that began the modern pattern of consumerization. In particular the rise of free, advertising-based services such as email and search engines from companies like Hotmail and Yahoo! began to establish the idea that consumer IT offerings based on a simple Internet browser were often viable alternatives to traditional business computing approaches. In recent years, this view has become increasingly accepted due to the widespread reliance on free, advertising-based services from a growing number of firms such as Google, Facebook and Twitter .
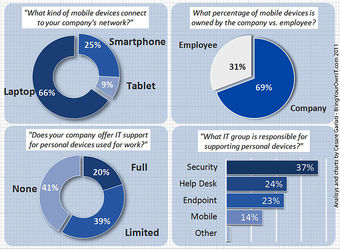
Consumerization Facts – Part 2
The report also found that a strategic approach to consumerization starts with providing IT support to personal devices.
Business Implications
The primary impact of consumerization is that it is forcing businesses, especially large enterprises, to rethink the way they procure and manage IT equipment and services. Historically, central IT organizations controlled the great majority of IT usage within their firms—choosing or, at least, approving the systems and services that employees used. Today, employees and departments are becoming increasingly self-sufficient in meeting their IT needs. Products have become easier to use, and cloud-based, software-as-a-service offerings are addressing an ever-widening range of business needs in areas such as video-conferencing, digital imaging, business collaboration, salesforce support and systems back-up.
Equally important is the fact that large enterprises have become increasingly dependent upon consumerized services that provide search capabilities, mapping, and social interaction. The capabilities of firms such as Google, Facebook and Twitter are now essential components of many firms’ marketing strategies. One of the most important consumerization questions going forward is to what extent such advertising-based services will spread into major corporate applications such as email, Customer Relationship Management (CRM), and Intranets.
One of the more serious, negative implications of consumerization is that security controls have been slower to be adopted in the consumer space. As a result, there is an increased risk to the information assets accessed through these less trustworthy consumerized devices . This shortcoming may soon be remedied by the chip manufacturers through technologies such as Intel’s “Trusted Execution Technology” and ARM’s “Trust Zone. “
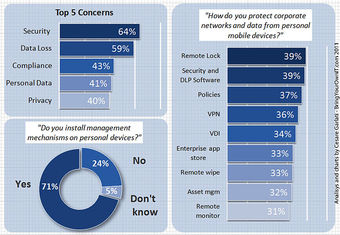
Consumerization Facts – Part 3
Lastly, the report found that new IT tools reduce security risks and management costs.
Technology Implications
In addition to the mass market changes above, consumer markets are now changing large scale computing as well. The giant data centers that have been and are being built by firms such as Google, Apple, Amazon and others are far larger and generally much more efficient than the data centers used by most large enterprises. For example, Google is said to support over 300 million Gmail accounts, while executing more than 1 billion searches per day. Supporting these consumer-driven volumes requires new levels of efficiency and scale, and this is transforming many traditional data center approaches and practices. Among the major changes are reliance on low cost, commodity servers, N+1 system redundancy, and largely unmanned data center operations.
20.1.3: Types of Networks
Networks are often classified by their physical or organizational extent, their purpose, their usage, trust level, and access rights.
Learning Objective
Compare the usage, trust level, and access rights of the main technology networks
Key Points
- A personal area network (PAN) is a computer network used for communication among computer and information technological devices close to one person.
- A local area network (LAN) is a network that connects computers and devices in a limited geographical area such as a home, school, computer laboratory, office building, or closely positioned group of buildings.
- A wide area network (WAN) is a computer network that covers a large geographic area such as a city, country, or even intercontinental distances, using a communications channel that combines many types of media such as telephone lines, cables, and air waves.
- A backbone network is part of a computer network infrastructure that interconnects various pieces of network, providing a path for the exchange of information between different LANs or subnetworks.
- A virtual private network (VPN) is a computer network in which some of the links between nodes are carried by open connections or virtual circuits in some larger network (e.g., the Internet) instead of by physical wires.
Key Term
- hypervisor
-
A software or firmware system that provides a virtual machine and allows it to operate directly on underlying hardware (instead of via emulation), but within specified constraints
Networks are often classified by their physical or organizational extent or their purpose. Usage, trust level, and access rights differ between these types of networks, outlined below.
Personal Area Network (PAN)
A personal area network (PAN) is a computer network used for communication among computer and information technological devices close to one person. Devices used in a PAN include personal computers, printers, fax machines, telephones, PDAs, scanners, and even video game consoles. Home area networks (HANs) are very similar to PANs.
Local Area Network (LAN)
A local area network (LAN) is a network that connects computers and devices in a limited geographical area such as home, school, computer laboratory, office building, or closely positioned group of buildings. Each computer or device on the network is a node. The defining characteristics of LANs, in contrast to WANs (wide area networks), include their higher data transfer rates, smaller geographic range, and no need for leased telecommunication lines. LANs can be connected to wide area networks by using routers.
Wide Area Network (WAN)
A wide area network (WAN) is a computer network that covers a large geographic area such as a city, country, or even intercontinental distances, using a communications channel that combines many types of media such as telephone lines, cables, and air waves. A WAN often uses transmission facilities provided by common carriers, such as telephone companies.
Storage Area Network (SAN)
A storage area network (SAN) is a dedicated network that provides access to consolidated, block level data storage. SANs are primarily used to make storage devices, such as disk arrays, tape libraries, and optical jukeboxes, accessible to servers so that the devices appear as locally-attached devices to the operating system. A SAN typically has its own network of storage devices that are not accessible through the local area network by other devices.
Campus Area Network (CAN)
A campus area network (CAN) is a computer network made up of an interconnection of LANs within a limited geographical area. The networking equipment (switches, routers) and transmission media (optical fiber, copper plant, Cat5 cabling, etc.) are almost entirely owned by the campus tenant or owner: an enterprise, university, government, etc. In the case of a university campus-based campus network, the network is likely to link a variety of campus buildings — including, for example, academic colleges or departments, the university library, and student residence halls. CANs are similar to metropolitan area networks (MANs), which usually span cities or large campuses.
Backbone Network
A backbone network is part of a computer network infrastructure that interconnects various pieces of network, providing a path for the exchange of information between different LANs or subnetworks. A backbone can tie together diverse networks in the same building, in different buildings in a campus environment, or over wide areas. Normally, the backbone’s capacity is greater than that of the networks connected to it.
A large corporation which has many locations may have a backbone network that ties all of these locations together — for example, if a server cluster needs to be accessed by different departments of a company which are located at different geographical locations. The equipment which ties these departments together constitute the network backbone. Network performance management, including network congestion, are critical parameters taken into account when designing a network backbone. Backbone networks are similar to enterprise private networks.
Virtual Private Network (VPN)
A virtual private network (VPN) is a computer network in which some of the links between nodes are carried by open connections or virtual circuits in some larger network (e.g., the Internet) instead of by physical wires. The data link layer protocols of the virtual network are said to be tunneled through the larger network when this is the case. One common application is secure communications through the public Internet, but a VPN need not have explicit security features, such as authentication or content encryption. VPNs, for example, can be used to separate the traffic of different user communities over an underlying network with strong security features.
Virtual Network
Not to be confused with a Virtual Private Network, a Virtual Network defines data traffic flows between virtual machines within a hypervisor in a virtual computing environment. Virtual Networks may employ virtual security switches, virtual routers, virtual firewalls, and other virtual networking devices to direct and secure data traffic.
The Internet changed the way the world produces and consumes information
The Internet, represented in this photo, is an aggregation of the different computer networks spanning the globe.
20.2: Decision Making
20.2.1: Expert Systems
An expert system consists of both an inference engine and a knowledge base and has decision-making abilities.
Learning Objective
Break down expert systems to the inference engine, the knowledge base, and conversational
Key Points
- In the 1980s, a third component was added to most expert systems: A dialog interface to communicate with users. This ability to conduct a conversation with users was later called “conversational. “
- In expert system technology, the knowledge base is expressed with natural language rules, such as if-then statements. For example: “If it is living then it is mortal. ” This dialog interface has the advantage of speaking in everyday language, which is very rare in computer science.
- Knowledge-based systems are artificial intelligent tools working in a narrow domain to provide intelligent decisions with justification. Knowledge is acquired and represented using various knowledge representation techniques, rules, frames and scripts.
Key Terms
- artificial intelligence
-
The branch of computer science dealing with the reproduction or mimicking of human-level intelligence, self-awareness, knowledge, conscience, thought in computer programs.
- knowledge base
-
A database designed to meet the complex storage and retrieval requirements of computerized knowledge management, especially in support of artificial intelligence or expert systems.
Example
- An expert system in use in the financial services field is its use during the approval process for mortgages. Loan departments tend to use expert systems for smaller amount mortgage requests because of the growing cost of labor, which makes the handling and acceptance of relatively smaller loans less profitable.
Definition of an Expert System
An expert system has a unique structure, different from traditional computer programs. It is divided into two parts: One fixed and independent of the expert system—the inference (reasoning) engine, and one variable—the knowledge base. To run an expert system, the engine uses the knowledge base in the same way that a human reasons. In the 1980s, a third component was added to most expert systems: A dialog interface to communicate with users. This ability to conduct a conversation with users was later called “conversational. ” In expert system technology, the knowledge base is expressed with natural language rules, such as “if-then” statements. For example: “If it is living then it is mortal. ” This dialog interface has the advantage of speaking in everyday language, which is very rare in computer science (a classic computer program must be written in a specific programming language in order for the computer to understand and carry out instructions) .

Robots Are a Type of Expert System.
Expert systems have decision-making abilities, just like their human counterparts.
Knowledge-based Systems
Knowledge based systems are artificial intelligent tools working in a narrow domain to provide intelligent decisions with justification. Knowledge is acquired and represented using various knowledge representation techniques, rules, frames and scripts. The basic advantages offered by such a system are documentation of knowledge, intelligent decision support, self learning, reasoning and explanation. Knowledge-based systems are systems based on the methods and techniques of artificial Intelligence. Their core components are
- Knowledge base
- Acquisition mechanisms
- Inference mechanisms (reasoning ability)
Knowledge base systems (KBS) go beyond the decision support philosophy to incorporate expert system technology into the decision-making framework. Expert systems (ES) have been the tools and techniques perfected by artificial intelligence (AI) researchers to deduce decision influences based on the codification of knowledge and applying rules, such as if-then statements.
20.2.2: Informed Decisions
Effectively transforming data into actionable information is the key to using information technology to improve decision making.
Learning Objective
Infer how managing information systems relates to decision-making
Key Points
- The decision-making process involves several steps, which includes the establishment of objectives, classification of objectives by order of importance, and the development of alternative actions.
- Business organizations utilize management information systems (MIS), which combine the use of information technology, people, and data/information to provide tools used in making decisions.
- An MIS supports a business’ long-range plans, providing performance analysis reports on areas critical to those plans, with feedback mechanisms that improve guidance for every aspect of the enterprise, including recruitment and training.
Key Term
- cost center
-
A division or project of an organization to which costs can be specifically allocated.
Decision-making Process
Decision making can be regarded as the mental processes (cognitive processes) resulting in the selection of a course of action among several alternative scenarios. Every decision making process produces a final choice. The output can be an action or an opinion of choice. A typical decision-making process involves several steps:
- Objectives must first be established;
- Objectives must be classified and placed in order of importance;
- Alternative actions must be developed;
- The alternatives must be evaluated against all the objectives;
- The alternative that is able to achieve all the objectives is the tentative decision;
- The tentative decision is evaluated for more possible consequences;
- The decisive actions are taken and additional actions are taken to prevent any adverse consequences from becoming problems, which can lead to the processes of problem analysis and decision-making to begin all over again.
Management Information Systems
Information technology refers to the convergence of audio-visual and telephone networks with computer networks through a single cable or link system that unifies signal distribution and management. Business organizations utilize management information systems (MIS), which combine the use of information technology, people, and data/information to provide tools used in making decisions . Management information systems are distinct from other information systems in that they are designed to be used to analyze and facilitate strategic and operational activities in the organization. An MIS supports a business’ long-range plans, providing performance analysis reports on areas critical to those plans, with feedback mechanisms that improve guidance for every aspect of the enterprise, including recruitment and training. MIS not only indicates how various aspects of a business are performing, but also why and where. MIS reports include near-real-time performance of cost centers and projects with detail sufficient for individual accountability.

Smartphones Make It Easier for Individuals to Make Informed Decisions.
Technology enables fast access to vast quantities of information, which can lead to better decision-making.
20.2.3: Information and Risk Trade-Off
IT risk relates to the business risk associated with the use, ownership, operation, involvement, and adoption of IT within an enterprise.
Learning Objective
Explain how organizations can measure and control IT risk
Key Points
- IT risk encompasses, not only the negative impact on operations and service delivery which can bring destruction or reduction of the organization’s value, but also the benefit\value enabling risk associated with missed opportunities to use technology or the improper management of IT projects.
- The measure of IT risk can be determined as a product of threat, vulnerability and asset values or Risk = Threat * Vulnerability * Asset Value.
- IT risk management can be considered a component of a wider enterprise risk management (ERM) system. Some organizations have a comprehensive enterprise risk management methodology, which addresses four objective categories: strategy, operations, financial reporting, and compliance.
Key Terms
- COSO
-
Committee of Sponsoring Organizations of the Treadway Commission (COSO) is a voluntary private-sector organization dedicated to providing thought leadership to executive management and governance entities on aspects of organizational governance, business ethics, internal control, enterprise risk management, fraud and financial reporting.
- likelihood
-
The probability of a specified outcome; the chance of something happening; probability; the state of being probable.
Measuring IT Risk
Information technology (IT) risk involves the business risk associated with the use, ownership, operation, involvement, influence and adoption of IT within an enterprise. IT encompasses not only the negative impact on operations and service delivery, but also the benefit and/or value enabling risk associated with missed opportunities to use technology to enable or enhance the business (including improper management of IT projects). The negative impact can cause destruction or reduction of the organization’s value. The benefit and/or enabling risk can result in overspending or late delivery of projects that lead to adverse business results.
Risk is the product of the likelihood of an occurrence times its impact (Risk = Likelihood x Impact). The measure of IT risk can be determined as a product of threat, vulnerability, and asset values (Risk = Threat x Vulnerability x Asset Value).
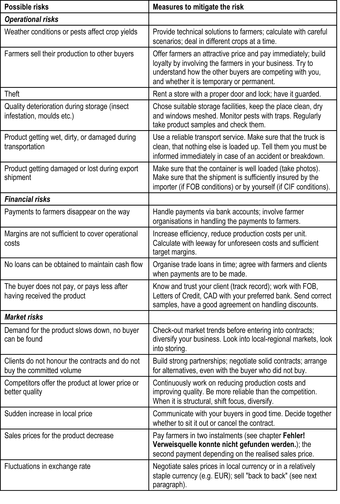
Possible Business Risks
This chart represents a list of the possible risks involved in running an organic business. Risks such as these affect sales, which in turn affect the amount of operating leverage a company should utilize.
IT and Enterprise Risk Management
IT risk management can be viewed as a component of a wider enterprise risk management (ERM) system. Some organizations have a comprehensive enterprise risk management methodology in place. The four objective categories addressed in an ERM, according to COSO, are:
- Strategy – high-level goals, aligned with and supporting the organization’s mission
- Operations – effective and efficient use of resources
- Financial Reporting – reliability of operational and financial reporting
- Compliance – compliance with applicable laws and regulations
IT risk transverses all four of the aforementioned categories and should be managed within the framework of enterprise risk management. Risk appetite and risk sensitivity of the whole enterprise should guide the IT risk management process. ERM should provide the context and business objectives on the management of IT risk.
20.2.4: Information and Knowledge
Knowledge is acquired through the use of and access to information.
Learning Objective
Explain the process of transforming information into knowledge
Key Points
- Information seeking is the process or activity of attempting to obtain information in both human and technological contexts. Information seeking is related to, but different from, information retrieval.
- Retrieving information is an integral part of information gathering and with today’s technology it can involve searching for documents, for information within documents, and for metadata about documents,. It may also involve searching structured storage, relational databases, and the Internet.
- Both information access and information architecture can facilitate user access to vast quantities of information and the use of it.
Key Terms
- relational database
-
A database consisting of separate tables, having explicitly defined relationships, and whose elements may be selectively combined as the results of queries.
- metadata
-
Data that describes other data, serving as an informative label.
- database
-
a collection of information in a regular structure, usually, but not necessarily in a machine-readable format accessible by a computer
Using and Managing Information
Information seeking is the process or activity of attempting to obtain information in both human and technological contexts. Information seeking is related to, but different from, information retrieval. Retrieving information is an integral part of information gathering and with today’s technology it can involve searching for documents, for information within documents, and for metadata about documents. Receiving information can also involve searching structured storage, relational databases, and the Internet. Information management (IM) is the collection and management of information from one or more sources and the distribution of that information to one or more audiences. Sometimes this involves those who have a stake in, or a right to that information. Management means the organization of and control over the structure, processing and delivery of information .
Information Presented in a Software Application
Well-organized information improves knowledge and decision making.
Knowledge Through Information
Knowledge is acquired through the use of and access to information. An area of research known as information access aims to automate the processing of large and unwieldy amounts of information and to simplify users’ access to it. Applicable technologies include information retrieval, text mining, machine translation, and text categorization. Information architecture (IA) is the art and science of organizing and labeling websites, intranets, online communities and software to support information use. It is an emerging discipline and community of practice focused on bringing together principles of design and architecture to the digital landscape. Typically it involves a model or concept of information which is used and applied to activities that require explicit details from complex programs and information systems. These activities include library systems and database development.
20.2.5: Data and Information
Data consists of nothing but facts, which can be manipulated to make it useful; the analytical process turns the data into information.
Learning Objective
Explain the process of turning data into information
Key Points
- Data are the numbers, characters, or symbols on which operations are performed by a computer, being stored and transmitted in the form of electrical signals and recorded on magnetic, optical, or mechanical recording media.
- In order to be processed by a computer, data needs to be first converted into a machine readable format. Once data is in digital format, various procedures can be applied on the data to get useful information.
- Data processing may involve various processes, including: data summarization, data aggregation, data validation, data tabulation, and statistical analysis.
Key Terms
- statistical analysis
-
The process of examining data to draw conclusions or insights, and determine cause-and-effect patterns between events; for example determining the safety and efficacy of new drugs by drawing out a probability as to whether the fact that a patient got better (or worse) was due to the drug or some other (perhaps random) factor.
- tabulation
-
A table displaying data in compact form.
- primary data
-
information collected by the investigator conducting the research
- secondary data
-
information collected by someone other than the user of the data
Forms of Computer Data
Data are the numbers, characters, or symbols on which operations are performed by a computer, being stored and transmitted in the form of electrical signals and recorded on magnetic, optical, or mechanical recording media. A program is a set of data that consists of a series of coded software instructions to control the operation of a computer or other machine. While program files are referred to as executable files, they may also contain data which is built into the program. For example, some programs have a data segment, which contains constants and initial values. Binary files (readable by a computer but not a human) are sometimes called “data” and are distinguishable from human-readable data, referred to as “text” .
Changing Technology Has Improved The Way Data Is Organized.
Computer systems make it easier to turn data into useful information.
Data vs. Information
Data consists of nothing but facts (organized or unorganized) which can then be manipulated into other forms to make it useful and understandable, turning the data into information. The process of manipulating facts to information is referred to as “processing. ” In order to be processed by a computer, data needs to first be converted into a machine readable format. Once data is in digital format, various procedures can be applied on the data to get useful information. Data processing may involve various processes, including:
- Data summarization
- Data aggregation
- Data validation
- Data tabulation
- Statistical analysis
Data processing may or may not be distinguishable from data conversion, which involves changing data into another format, and does not involve any data manipulation. During processing, raw data is used as an input to produce information as an output, typically in the form of reports and other analytical tools.
20.3: E-Commerce
20.3.1: Selling to Businesses
B2B e-commerce is the type of e-commerce that deals with relationships between and among businesses.
Learning Objective
Explain the impact of technological advances on business to business (B2B) commerce
Key Points
- About 80% of e-commerce is of this type, and most experts predict that B2B e-commerce will continue to grow faster than the business to consumer (B2C) segment.
- E-frastructure is the architecture of B2B, primarily consisting of logistics, application service providers, outsourcing of e-commerce functions, auction solutions, content management software, and Web-based commerce enablers.
- E-markets are simply defined as Web sites where buyers and sellers interact with each other and conduct transactions.
- Impacts of B2B e-commerce on the economy in general are evident in transaction costs, disintermediation, transparency in pricing, and economies of scale and network effects.
Key Terms
- outsourcing
-
The transfer of a business function to an external service provider.
- e-commerce
-
Commercial activity conducted via the Internet.
Business to business (B2B) e-commerce is simply defined as e-commerce between companies. This is the type of e-commerce that deals with relationships between and among businesses. About 80% of e-commerce is of this type, and most experts predict that B2B e-commerce will continue to grow faster than the business to consumer (B2C) segment. The B2B market has two primary components: e-frastructure and e-markets. E-frastructure is the architecture of B2B, primarily consisting of a number of subcategories:
- Logistics: transportation, warehousing and distribution
- Application service providers: deployment, hosting and management of packaged software from a central facility
- Outsourcing of functions in the process of e-commerce, such as Web-hosting, security and customer care solutions
- Auction solutions software for the operation and maintenance of real-time auctions in the Internet
- Content management software for the facilitation of Web site content management and delivery
- Web-based commerce enablers
E-markets are simply defined as Web sites where buyers and sellers interact with each other and conduct transactions.
The more common B2B examples and best practice models are IBM, Hewlett Packard (HP), Cisco, and Dell. Cisco, for instance, receives over 90% of its product orders over the Internet. Most B2B applications are in the areas of supplier management (especially purchase order processing), inventory management (i.e., managing order-ship-bill cycles), distribution management (especially in the transmission of shipping documents), channel management (i.e., information dissemination on changes in operational conditions), and payment management (e.g., electronic payment systems or EPS).
Impacts of B2B e-commerce on the economy in general are evident in a number of areas:
- Transaction costs: There are three cost areas that are significantly reduced through the conduct of B2B e-commerce. First is the reduction of search costs, as buyers need not go through multiple intermediaries to search for information about suppliers, products, and prices as in a traditional supply chain. In terms of effort, time, and money spent, the Internet is a more efficient information channel than its traditional counterparts. In B2B markets, buyers and sellers are gathered together into a single online trading community, reducing search costs even further. Second is the reduction in the costs of processing transactions (e.g. invoices, purchase orders and payment schemes), as B2B allows for the automation of transaction processes and, therefore, the quick implementation of the same compared to other channels (such as the telephone and fax). Efficiency in trading processes and transactions is also enhanced through the B2B e-market’s ability to process sales through online auctions. Third, online processing improves inventory management and logistics.
- Disintermediation: Through B2B e-markets, suppliers are able to interact and transact directly with buyers, thereby eliminating intermediaries and distributors. However, new forms of intermediaries are emerging. For instance, e-markets themselves can be considered intermediaries because they come between suppliers and customers in the supply chain.
- Transparency in pricing: Among the more evident benefits of e-markets is the increase in price transparency. The gathering of a large number of buyers and sellers in a single e-market reveals market price information and transaction processing to participants. The Internet allows for the publication of information on a single purchase or transaction, making the information readily accessible and available to all members of the e-market. Increased price transparency has the effect of pulling down price differentials in the market. In this context, buyers are provided much more time to compare prices and make better buying decisions. Moreover, B2B e-markets expand borders for dynamic and negotiated pricing wherein multiple buyers and sellers collectively participate in price-setting and two-way auctions. In such environments, prices can be set through automatic matching of bids and offers. In the e-marketplace, the requirements of both buyers and sellers are thus aggregated to reach competitive prices, which are lower than those resulting from individual actions.
- Economies of scale and network effects: The rapid growth of B2B e-markets creates traditional supply-side cost-based economies of scale. Furthermore, the bringing together of a significant number of buyers and sellers provides the demand-side economies of scale or network effects. Each additional incremental participant in the e-market creates value for all participants in the demand side. More participants form a critical mass, which is key in attracting more users to an e-market.

B2B E-Commerce
E-commerce has become so prevalent in today’s business world that multiple conferences are held each year — like this one pictured in the UK.
20.3.2: Selling to Consumers
B2C e-commerce involves customers gathering information and purchasing either physical or information goods over an electronic network.
Learning Objective
Explain how technological change has transformed the business-to-consumer (B2C) industry
Key Points
- Information goods include electronic material or digitized content, such as software or e-books, and can be delivered over an electronic network.
- The more common applications of this type of e-commerce are in the areas of purchasing products and information, and personal finance management, which pertains to the management of personal investments and finances with the use of online banking tools.
- B2C e-commerce reduces transactions costs (particularly search costs) by increasing consumer access to information and allowing consumers to find the most competitive price for a product or service.
- B2C e-commerce also reduces market entry barriers since the cost of putting up and maintaining a website is much cheaper than installing a “brick-and-mortar” structure for a firm.
- C2C e-commerce is characterized by the growth of electronic marketplaces and online auctions, particularly in vertical industries where firms/businesses can bid for what they want from among multiple suppliers.
Key Term
- distribution
-
The process by which goods get to final consumers over a geographical market, including storing, selling, shipping, and advertising.
Business-to-consumer (B2C) e-commerce, or commerce between companies and consumers, involves customers gathering information; purchasing physical goods (i.e., tangibles such as books or consumer products) or information goods (or goods of electronic material or digitized content, such as software or e-books); and, for information goods, receiving products over an electronic network. It is the second largest and the earliest form of e-commerce. Its origins can be traced to online retailing (or e-tailing). Thus, the more common B2C business models are the online retailing companies such as Amazon.com, Drugstore.com, Beyond.com, Barnes and Noble, and Toys-R-Us. Other B2C examples involving information goods are E-Trade and Travelocity.
The more common applications of this type of e-commerce are in the areas of purchasing products and information, and personal finance management, which pertains to the management of personal investments and finances with the use of online banking tools (e.g., Quicken). Online retailing transactions make up a significant share of the B2C e-commerce market.
B2C e-commerce reduces transactions costs (particularly search costs) by increasing consumer access to information and allowing consumers to find the most competitive price for a product or service. B2C e-commerce also reduces market entry barriers since the cost of putting up and maintaining a website is much cheaper than installing a “brick-and-mortar” structure for a firm. In the case of information goods, B2C e-commerce is even more attractive because it saves firms from factoring in the additional cost of a physical distribution network. Moreover, for countries with a growing and robust Internet population, delivering information goods becomes increasingly feasible.
Another form of e-commerce involving selling to consumers is known as consumer-to-consumer (C2C). It is simply commerce between private individuals or consumers. This type of e-commerce is characterized by the growth of electronic marketplaces and online auctions, particularly in vertical industries where firms/businesses can bid for what they want from among multiple suppliers. It perhaps has the greatest potential for developing new markets.
This type of e-commerce comes in at least three forms:
- Auctions facilitated at a portal, such as eBay, which allows online real-time bidding on items being sold in the Web
- Peer-to-peer systems, such as the Napster model (a protocol for sharing files between users used by chat forums similar to IRC) and other file exchange and later money exchange models
- Classified ads at portal sites such as Craigslist (an interactive, online marketplace where buyers and sellers can negotiate and that features “Buyer Leads & Want Ads”)
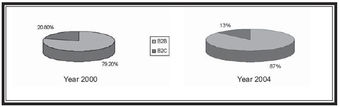
B2C E-Commerce
B2C e-commerce makes up a smaller portion of the market share of e-commerce compared to B2B, and appears to be shrinking in comparison.
20.4: Difficulties with New Technologies
20.4.1: Forced Entry
Cybercrimes are those committed via computer networks for such purposes as fraud, identity theft, and the hacking of sensitive information.
Learning Objective
Discuss the ramifications of cybercrime
Key Points
- Cybercrimes are offenses that are committed with a criminal motive to intentionally harm the reputation of the victim or cause physical or mental harm directly or indirectly, using modern telecommunication networks such as the Internet and mobile phones.
- Computer crime may be divided into two categories: crimes that target computers directly, and crimes facilitated by computer networks or devices, the primary target of which is independent of the network or device.
- Computer fraud is any dishonest misrepresentation of fact intended to get another to do or refrain from doing something which causes loss.
- Identity theft is a form of stealing someone’s identity in which someone pretends to be someone else by assuming that person’s identity, typically in order to access resources or obtain credit and other benefits in that person’s name.
Key Terms
- hacking
-
Unauthorized attempts to bypass the security mechanisms of an information system or network. See also cracker.
- phishing
-
The act of sending email that falsely claims to be from a legitimate organization. This is usually combined with a threat or request for information. For example, it may claim that an account will close, a balance is due, or information is missing from an account. The email will ask the recipient to supply confidential information, such as bank account details, PINs or passwords; these details are then used by the owners of the website to conduct fraud.
- identity theft
-
The deliberate assumption of another person’s identity, usually to gain access to that person’s finances or to frame a person for a crime.
Forced Entry
The creation and widespread use of new technology brings along with it many benefits. However, new and previously unaccounted-for dangers arise as well. Cybercrime is one such danger. It is defined as offenses that are committed against individuals or groups of individuals with a criminal motive to intentionally harm the reputation of the victim or cause physical or mental harm to the victim, directly or indirectly, using modern telecommunication networks such as the Internet (chat rooms, emails, notice boards, etc.) and mobile phones (SMS/MMS). Such crimes may threaten a nation’s or individual’s security and financial health. Issues surrounding this type of crime have become high-profile, particularly those surrounding hacking, copyright infringement, and child abduction. There are also problems of privacy when confidential information is lost or intercepted, lawfully or otherwise.
Computer crime encompasses a broad range of activities. Generally, however, it may be divided into two categories: crimes that target computers directly, and crimes facilitated by computer networks or devices, the primary target of which is independent of the network or device. Crimes that primarily target computer networks or devices include computer viruses, denial-of-service attacks, and malware. Crimes that use computer networks or devices to advance other ends include cyberstalking, fraud and identity theft, information warfare, and phishing scams.
Computer Fraud
Computer fraud is any dishonest misrepresentation of fact intended to get another to do or refrain from doing something which causes loss. In this context, the fraud will result in obtaining a benefit by one of a number of means:
- Altering computer input in an unauthorized way. This requires little technical expertise and is not an uncommon form of theft by employees. Altering data before entry or entering false data, or entering unauthorized instructions or using unauthorized processes are the most common examples.
- Altering, destroying, suppressing, or stealing output, usually to conceal unauthorized transactions. This is difficult to detect.
- Altering or deleting stored data.
- Altering or misusing existing system tools or software packages, or altering or writing code for fraudulent purposes.
Other forms of fraud may be facilitated using computer systems, including bank fraud, identity theft, extortion, and theft of classified information.
Identity Theft
Identity theft is a form of stealing a person’s identity in which someone pretends to be someone else, typically in order to access resources or obtain credit and other benefits in that person’s name. The victim of identity theft (here meaning the person whose identity has been assumed by the identity thief) can suffer adverse consequences if he or she is held accountable for the perpetrator’s actions. Identity theft occurs when someone uses another’s personally identifying information, like name, Social Security number, or credit card number, without permission, to commit fraud or other crimes.
Identity fraud is often but not necessarily the consequence of identity theft. Someone can steal or misappropriate personal information without then committing identity theft using the stolen information; this can happen when a major data breach occurs and the information of a large number of people is compromised.
Documented Cases of Cybercrime
One of the highest profiled banking computer crimes occurred during a course of three years, beginning in 1970. The chief teller at the Park Avenue branch of New York’s Union Dime Savings Bank embezzled over $1.5 million from hundreds of accounts.
In 1983, a nineteen-year-old UCLA student used his PC to break into a Defense Department international communications system.
Between 1995 and 1998, the Newscorp satellite pay-to-view encrypted SKY-TV service was hacked several times during an ongoing technological arms race between a pan-European hacking group and Newscorp. The original motivation of the hackers was to watch Star Trek re-runs in Germany, which was something Newscorp did not have the copyright to allow.
In February 2000, an individual under the alias of MafiaBoy began a series denial-of-service attacks against high profile websites, including Yahoo!, Amazon.com, Dell, E*TRADE, eBay, and CNN. About 50 computers at Stanford University, as well as computers at the University of California at Santa Barbara, were among the zombie computers sending pings in DDoS attacks. On August 3, 2000, Canadian federal prosecutors charged MafiaBoy with 54 counts of illegal access to computers, plus a total of 10 counts of mischief to data for his attacks.
On March 2, 2010, Spanish investigators arrested three individuals for the infection of over 13 million computers around the world. The “botnet” of infected computers included PCs inside more than half of the Fortune 1,000 companies and more than 40 major banks, according to investigators.
In August 2010, the international investigation Operation Delego, operating under the aegis of the Department of Homeland Security, shut down the international pedophile ring Dreamboard. The website had approximately 600 members and may have distributed up to 123 terabytes of child pornography (roughly equivalent to 16,000 DVDs). To date, this is the single largest U.S. prosecution of an international child pornography ring; 52 arrests were made worldwide.

Cybercrime
Cybercrime can be committed using computer viruses and other various programs that can track any information you enter into computer networks.
20.4.2: Malware
Malware is software used or created by attackers to disrupt computer operation, gather sensitive information, or gain access to private computer systems.
Learning Objective
Explain how malware can negatively impact individuals and organizations
Key Points
- Malware includes computer viruses, worms, trojan horses, spyware, adware, and other malicious programs.
- Malware has caused the rise in use of protective software types such as anti-virus, anti-malware, and firewalls.
- Malware is often used against individuals to gain personal information such as social security numbers, bank or credit card numbers, and so on.
- Spyware is designed to monitor users’ web browsing, display unsolicited advertisements, or redirect affiliate marketing revenues to the spyware creator.
Key Terms
- malware
-
Software which has been designed to operate in a malicious, undesirable manner.
- adware
-
A software application that includes advertisements, which are displayed while the software is running. Developers use adware as a source of income and to keep the costs of the software down (usually making it free). Some adware programs can include spyware.
- spyware
-
Programs that surreptitiously monitor and report the actions of a computer user.
Malware
Malware, short for malicious (or malevolent) software, is software used or created by attackers to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It can appear in the form of code, scripts, active content, and other software. Malware is a general term used to refer to a variety of forms of hostile or intrusive software.
Malware includes computer viruses, worms, spyware, adware, and trojan horses . Malware is not the same as defective software, which is software that has a legitimate purpose but contains harmful bugs that were not corrected before release. However, some malware is disguised as genuine software, and may come from an official company website. An example of this is software used for harmless purposes that is packed with additional tracking software that gathers marketing statistics. Malware has caused the rise in use of protective software types such as anti-virus, anti-malware, and firewalls. Each of these are commonly used by personal users and corporate networks to stop the unauthorized access by other computer users, as well as the automated spread of malicious scripts and software.
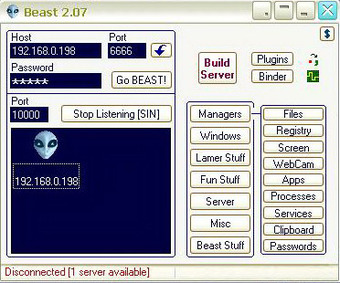
BEAST Trojan Horse
Beast, a Windows-based backdoor Trojan horse
The best-known types of malware, viruses and worms, are known for the manner in which they spread, rather than any specific types of behavior. The term computer virus is used for a program that has infected some executable software and, when run, causes the virus to spread to other executables. On the other hand, a worm is a program that actively transmits itself over a network to infect other computers. These definitions lead to the observation that a virus requires user intervention to spread, whereas a worm spreads itself automatically.
Purposes
Malware is sometimes used broadly against government or corporate websites to gather guarded information, or to disrupt their operation in general. However, malware is often used against individuals to gain personal information such as social security numbers, bank or credit card numbers, and so on. Left unguarded, personal and networked computers can be at considerable risk against these threats. Since the rise of widespread broadband Internet access, malicious software has more frequently been designed for profit. Since 2003, the majority of widespread viruses and worms have been designed to take control of users’ computers for black-market exploitation. Infected “zombie computers” are used to send email spam, to host contraband data such as pornography, or to engage in distributed denial-of-service attacks as a form of extortion.
Another strictly for-profit category of malware has emerged, called spyware. These programs are designed to monitor users’ web browsing, display unsolicited advertisements, or redirect affiliate marketing revenues to the spyware creator. Spyware programs do not spread like viruses; instead they are generally installed by exploiting security holes. They can also be packaged together with user-installed software, such as peer-to-peer applications.
The prevalence of malware as a vehicle for Internet crime, along with the challenge of anti-malware software to keep up with the continuous stream of new malware, has seen the adoption of a new mindset for individuals and businesses using the Internet. With the amount of malware currently being distributed, some percentage of computers will always be infected. For businesses, especially those that sell mainly over the Internet, this means that they need to find a way to operate despite security concerns. The result is a greater emphasis on back-office protection designed to protect against advanced malware operating on customers’ computers.
Concealment
For a malicious program to accomplish its goals, it must be able to run without being detected, shut down, or deleted. When a malicious program is disguised as something normal or desirable, users may willfully install it without realizing it. This is the technique of the Trojan horse or trojan. In broad terms, a Trojan horse is any program that invites the user to run it, though it conceals harmful or malicious code. The code may take effect immediately and can lead to many undesirable effects, such as deleting the user’s files or installing additional harmful software.
One of the most common ways that spyware is distributed is as a Trojan horse, bundled with a piece of desirable software that the user downloads from the Internet. When the user installs the software, the spyware is installed along with it. Spyware authors who attempt to act in a legal fashion may include an end-user license agreement that states the behavior of the spyware in loose terms, which users may not read or understand.
20.4.3: E-Mail as an Entry Point
Email represents a potential IT risk and entry point for hackers, and so IT teams must integrate appropriate safeguards.
Learning Objective
Understand the risks associated with organizational email systems and the tools available to offset those risks
Key Points
- Email is used by virtually every organization on the planet and is an often targeted weakness by hackers.
- Opening an email could potentially enable an executable file, which could contain a virus. Once this virus enters just one device, the shared professional network is at risk.
- Utilizing tools such as firewalls, anti-virus software, and encryption can help block attempts to hack via email.
- Organizations must be aware of the potential risks, and invest in IT accordingly to offset them.
Key Terms
- Firewall
-
A gateway between the internet and a local network, allowing or denying access based upon protocols.
- Encryption
-
A method of scrambling and unscrambling information to protect it during digital transmission (in the context of email).
Why Email is a Business Risk
Virtually every business and individual with internet access has an email account of some sort. Emails are files sent from one computer to another, and those files can contain virtually anything, including executable files. If a virus is transferred to a computer and executed internally, it can gain access to the device of an employee that has access to centralized databases. At this point, the virus has now infected the entire organization and, if not caught, can download, manipulate, export, and alter any and all customer data, strategic assets, and potentially even valuable IP.
As a result, protecting the inboxes of the employees at an organization is critical to minimizing this risk. There are a variety of mechanisms designed to do exactly that.
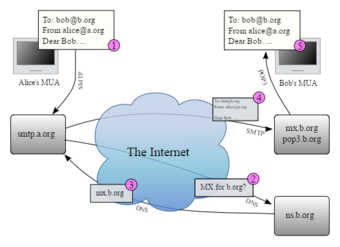
This image shows the transmission of an email from one device to another.
How to Protect Your Inbox
There are a few simple steps organizations should take to protect their email systems. These include:
- Firewalls – Simply put, a firewall permits or denies communication from the network based upon specific parameters. Setting stricter parameters with verification built in can stop viruses from accessing the network.
- Encryption – Encryption takes a message and scrambles the contents of that message upon sending. The sender must enable the receiver to unscramble that message, and this can be done in a variety of ways. For example, business partners may agree on a password that will unlock the contents of an email and verify the sender while protecting the contents during transmission.
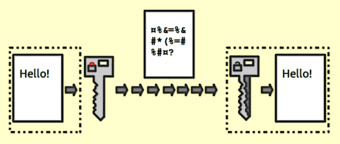
Encryption
This shows a simple visual representation of how encryption works.
- Anti-virus Software – Anti-virus programs are designed to record libraries of data on common viruses, and scan all incoming email traffic (as well as internal files and databases) for signs of malicious software.
- Intrusion detection systems (IDS) – Similar to anti-viruses, these programs scan devices and networks for malicious activity or violations to the preset policies.
As the world grows more and more digitally connected, the risks will continue to elevate. Being aware of the risks and investing in a strong IT infrastructure is key to mitigating the potential risks.
